Are there ways to explain the cryptography behind Grin with simpler terms? I’m led to believe there is because, when I first began to read about ElGamal cryptography, the texts were dense and hard to figure out what was going on, but once I read the implementation of it in code, all of that strange mathematical language became surprisingly simple to grasp. I can write the encryption, decryption, signature and verification in less than fifty lines of JavaScript! Here are the two brief equations that explains the cryptography of it. Given a generator “g” (which is about any integer greater than 1 and less than a prime number P), a secret “x” private key for the receiver of a message, some nonce “y” chosen by the sender of a message, we can send a secret number “a” in the range [1, p - 1] because these equations hold true (proof deferred, but you can obviously see it):
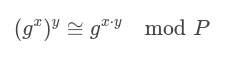
![]()
Why we can be confident that ElGamal Cryptography, given a prime of enough size (2048-bits), is secure? It’s because the receiver only publishes “g to the power of x” (which is the public key) for potential senders, keeping the secret “x” to oneself. it’s not feasible to calculate the private key, which is the exponent “x”, because this is the discrete logarithm problem. Can you easily solve the following equation? Try it and you’ll get the point of “asymmetric cryptography”.

I also noticed that, although there is “Elliptic Curve Cryptography” (ECC) and “ElGamal Cryptography”, they’re different implementations of the same thing: “Group Theory”. They’re both thought to be safe because of the “discrete logarithm problem”. Apparently, ECC is preferred because the non-prime number structure of the group prevents optimizations that would enable cryptanalysis (all groups in ElGamal Cyptography have a prime order), which is why the amount of points in an elliptic curve are counted and checked to not be prime. If my assumptions regarding the math of the whole of it do not fail me, the only difference is the key length: 256-bits of ECC versus 2048-bits of ElGamal.
So, is it possible to implement an almost-equivalent of Grin using ElGamal? This would greatly simplify the documents, as it would be possible to write code that explains what is going on. Even people that have concluded high school are likely to grasp ElGamal given “clock arithmetic”.

