Abstract
Asset security and transaction efficiency have always been concerned, so that digital cryptocurrencies based on blockchain are increasingly favored. In the transaction, it is necessary to effectively protect private information such as identity and transaction content through technical means. This survey investigates privacy-preserving techniques commonly used in cryptocurrencies, and comparatively analyzes the advantages and disadvantages of different methods. The work mainly covers three technical dimensions. First, this paper investigates and summarizes privacy issues in cryptocurrencies. Second, we investigate mainstream privacy preserving techniques, such as Mixer, Homomorphic Encryption, and State Channel. Specially, we focus on the development of Zero-Knowledge Proof schemes and analyze current defects. Finally, the future direction of blockchain privacy protection technology is prospected.
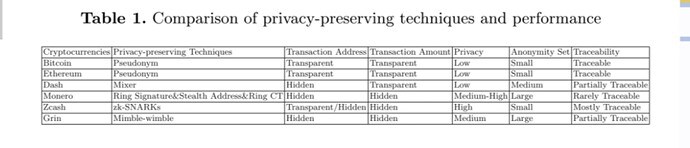
I wouldn’t say that Monero’s anonymity set is “High”. Likewise, I think Zcash has a much higher anonymity set than Monero, no?
Maybe due to the trusted setup that is needed by Zcash, as a result, third parties can reveal their identities.
In ia.cr/2020/1289 I describe a blockchain design that hides the transaction graph from Blockchain Analyzers. The insight in this technical note is that the block creator (the miner) can be restricted to the task of ensuring no double spends. The task of actually verifying transaction balances really belongs to the receiver. The bulk of the transaction can thus be encrypted in such a manner that double spends are disallowed and that only the receiver can decrypt and examine it. It allows the receiver to work her way back though the chain until she arrives at the coin generation blocks and completely verify the validity of the transaction. Since transactions on the blockchain are encrypted and the source of funds hidden, a global blockchain analyzer cannot create a general transaction graph.
The table above states that zk-SNARK is not quantum attack proof. However, I thought that I red long time ago that Grin used some tricks in order to protect against quantum computing attacks. Does anyone know how Grin protects against quantum attacks Or did my brain mix in some magical property that Grin does not have, which could easily happen with such a magical coin 
My understanding is that we also commit to the value with a hash (which is secure against quantum computers). This is not used, but it can be “turned on”. If it is turned on, then you need to publicly reveal the value if you want to spend a utxo
Switch commitments. We could convert all UTXOs to another quantum resistant crypto using switch commitments.
Good to have a contingency plan @johndavies24. But I thought Grin was already made quantum computing resistant, I have to trace back where I red it.
Mimblewimble outputs are Pedersen Commitments, which are not quantum-resistant. But by ‘embedding’ a hash of an ElGamal Commitment into each of our commitments (i.e. using it to generate blinding factors), we basically allow a doomsday switch to be activated via a softwork, in which the commitment scheme can be simply be changed.
This document really does a fantastic job at explaining it.